Deployment of an Active Directory Certificate Services (AD CS) on a corporate environment could allow system administrators to utilize it for establishing trust between different directory objects. However, it could allow red team operators to conduct an NTLM relay attack towards the web interface of an AD CS in order to compromise the network. The web interface is used for allowing users to obtain a certificate (web enrollment), is over HTTP protocol, doesn’t support signing and accepts NTLM authentication.
The details of the attack have been presented by Will Schroeder and Lee Christensen in the Certified Pre-Owned whitepaper. The attack forces the domain controller machine account (DC$) to authenticate towards a host which NTLM relay is configured. The authentication is relayed towards the Certificate Authority (CA) and raises a request for a certificate. Once the certificate is generated for the DC$ account an attacker could use this perform arbitrary operations on the domain controller such as retrieving the hash of the Kerberos account in order to create a golden ticket and establish domain persistence or dump hashes of domain administrators and establish a communication channel with the domain controller.
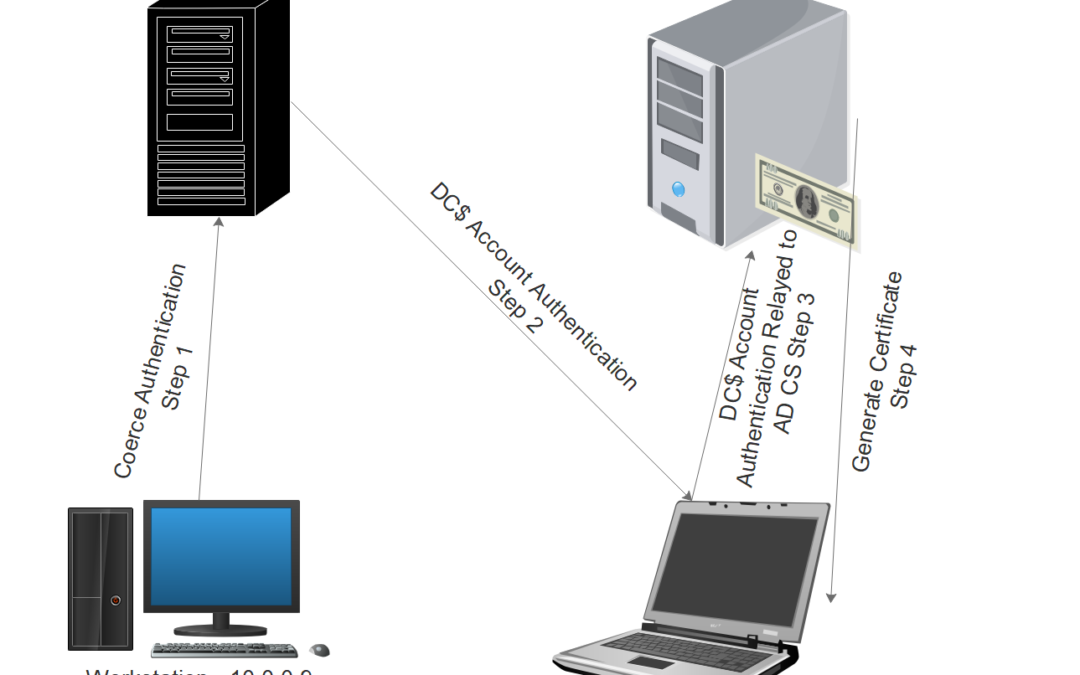
Active Directory Certificate Services can be installed as a role on the domain controller or in an individual server which is part of the domain. The following diagram illustrates the steps of the attack:
The attack requires identification of the certification authority. The “certutil” binary is a command line tool which can be used to dump and display certification authority information, verify certificates etc. Therefore it could be used as a quick way to discover if there is a certificate authority deployed on the domain.
The server name has been identified as “ca.purple.lab” and the web enrollment service is accessible over HTTP on the following URL:
From a non domain-joined system executing the “ntlmrelayx.py” from Impacket suite will configure various listeners (SMB, HTTP, WCF) that will capture the authentication from the domain controller machine account and relay that authentication information towards the active directory certification authority server.
The force authentication could be triggered by the proof of concept that Lionel Gilles developed called PetitPotam. This is achieved by exploiting the MS-EFSRPC protocol to make an API call (EfsRpcOpenFileRaw) that will trigger the machine account on the target to authenticate to another system. It could be executed by supplying standard user credentials and using the IP of the system which NTLM Relay is configured and the IP address of the CA.
This attack could be also executed even if credentials are not supplied. Access to the network even without credentials could lead to domain compromise if a certificate authority is deployed without preventive measures on the domain controller instead of a different server.
If the following output is displayed this will constitute that the attack was successful and authentication has been triggered.
Alternatively, if initial access has been established to a domain joined system the binary can be used instead.
As with the majority of the attacks, Benjamin Delpy has also implemented authentication trigger in newer versions of Mimikatz. Using the encrypting file system (EFS) module, and specifying the domain controller and the host acting as NTLM Relay will send the remote procedure call.
There is also a PowerShell implementation of PetitPotam attack which was developed by S3cur3Th1sSh1t following the Mimikatz module.
All the above triggers will coerce the DC$ account (machine account on the domain controller) to authenticate towards the certificate authority.
Since the attack requires either the web service component to be installed or the web enrollment a request will be raised for a certificate under the DC$ account. The certificate will be generated for the account in Base64 format.
The obtained certificate can be used with Rubeus in order to request a Kerberos ticket (Ticket Granting Ticket) for the machine account which is a high privileged account on the domain controller.
The ticket will imported into the current session of the user. Since this ticket belongs to the DC$ account can be used to conduct a range of activities in order to compromise the domain such as retrieve the NTLM hash of the “krbtgt” account and create a golden ticket, establish a connection with the domain controller via WMI, perform pass the hash etc.
Running the following command will verify that the ticket is cached into the current logon session.
Since the ticket is cached the DCSync technique can be used to retrieve the hash of the “krbtgt” account in order to create the golden ticket and establish domain persistence.
Similarly the password hash for the user “Administrator” could be retrieved. This user is a member of the “Domain Administrators” group.
The hash value could be used with “wmiexec” from Impacket in order to establish a session to the domain controller as domain administrator.
Alternatively, Mimikatz or any other similar tooling could be used to perform the pass the hash technique. Executing the following command in Mimikatz will create another session as the user “Administrator“.
From the new session the drive C$ can be mapped in order to access the domain controller file system.
An alternative tool which implements the attack (ADCSPwn) was developed in C# by batsec and can be used within Cobalt Strike via “execute-assembly” or with any other similar red teaming framework like Covenant. The obvious benefit is that the attack could be executed directly from memory without the need to drop anything to disk or to use another system as a relay in order to pass the authentication to the CA. ADCSPwn set up a relay server locally and coerce the authentication by making an API call (EfsRpcOpenFileRaw).
The certificate will be generated into the console in Base64 format.
However, it should be noted that the attack only works if the “WebClient” service is running on the domain controller. By default this service is not installed and therefore it is unlikely that direct execution of the tool will lead to the expected results.
The “WebClient” service is created when the “WebDav Redirector” feature is installed on the server.
This content was originally published here.